What's new?
- More intelligible API limits view. VirusTotal API keys are governed by a set of privileges and consumption quotas. Consumption quotas dictate how many lookups a given user can perform in a given time frame. There are three different types of quotas that can apply to API keys: per minute, per day and per month. If you consume your per minute allowance, you will be unable to retrieve any further information from the API until the next minute. The same goes for the daily limit and monthly limits. In other words, the most limiting quota is enforced. This often led users to misunderstandings. We have revamped the user API key and the premium group API key views in an effort to make things more understandable, similarly, we have introduced shortcuts to common tools and documentation for the API:

- Onboarding handholding. At VirusTotal we are committed to making our users successful. We want you to become power users and we want to make sure our platform aligns to your goals. New users added to VT ENTERPRISE groups are now receiving some onboarding tips and materials. For now these mostly point to our golden use cases outlined in our Getting Started guide.
What's fixed?
- Session not found bug in VTDIFF. VTDIFF is a VT HUNTING component that allows users to automatically identify optimal binary patterns to detect a group of files and build YARA rules with these. Recent improvements had introduced a transient bug whereby a "Not found" view was being displayed upon launching a new VTDIFF job. This has now been fixed and you should no longer see this random behaviour.
What's new?
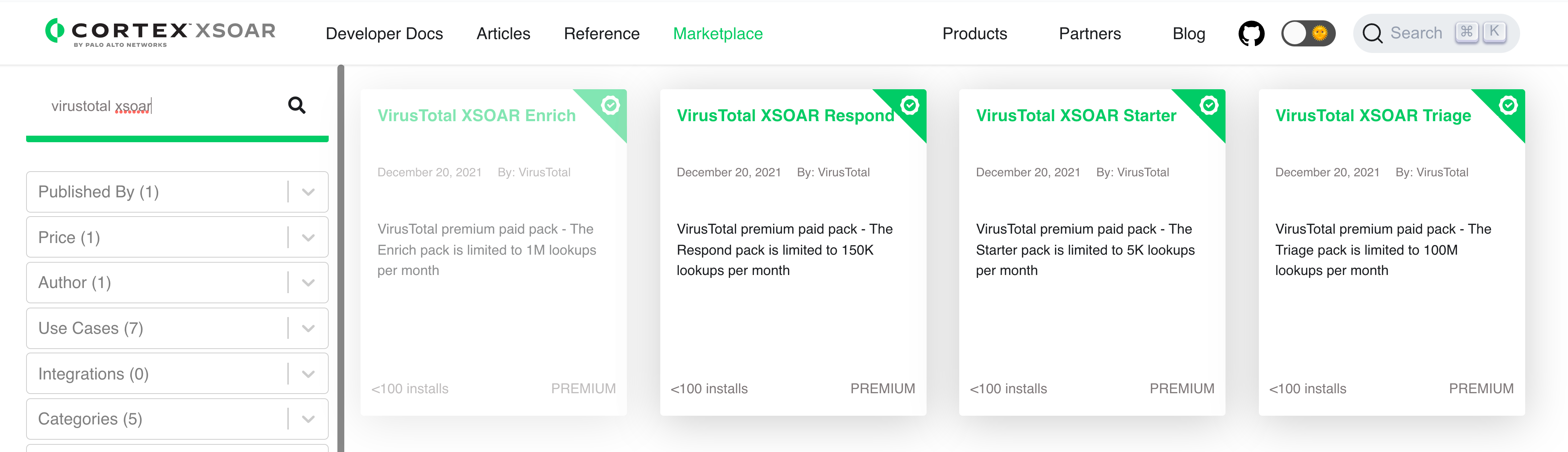
- Premium VT API packs in the Palo Alto Cortex XSOAR marketplace. We have published 4 new premium VT API packs in the Palo Alto Cortex XSOAR marketplace. XSOAR (formerly Demisto), is a Security Orchestration Automation and Response platform that allows companies to collect threat-related data from a range of sources (SIEM, Firewall, IDS, etc.) and automate the responses to the threat. Palo Alto Networks customers can now spend their credits towards the VirusTotal integration to contextualize incidents with superior crowdsourced visibility and perform more effective triage through multi-angular detection (sandboxing, YARA analysis, SIGMA behavioural flags, antivirus scanning, etc.).
- Vir.IT file scanner. Since our last release notes update we have added a new malware scanning engine to VirusTotal: Vir.IT eXplorer PRO. You can read more about this inclusion in the welcome post. Similarly, you can see it in action detecting a file in this VirusTotal report.
- VirusTotal Collections. Since our last release notes we have also launched some major functionality to allow users to share collections of IoCs (hashes, domains, IP addresses and URLs) among themselves in a more actionable and contextualized manner. You can read more about this in the Introducing VirusTotal Collections blog post, you can also easily create collections via command-line.
What's improved?
- New VirusTotal collections sources for additional contextualization. The aforementioned VirusTotal Collections functionality is not only driven by user contributions, VirusTotal is also crowdsourcing relevant threat information sources such as AlienVault OTX, Malpedia or Abuse.ch. In this development iteration we have added two new sourced:
- Sicehice - Sicehice fingerprints common attacker infrastructure and aggregates data from a number of sources in a way that is more easily searchable.
- Zeusmuseum - The Zeus banking malware has been a fixture within the cybercrime landscape since 2006. With the release of its source code in 2011, Zeus has splintered into many different malware families. The goal of the zeusmuseum. is to find, categorize, and lightly document every version of these Zeus-derived families.





