What’s new?
- Holistic search across IoCs and adversary intelligence knowledge cards. VirusTotal’s Threat Landscape module incorporates {attribution, threat actor, campaign, toolkit} knowledge cards into our top VirusTotal packages. As of now, whenever you perform free text searches in VirusTotal (e.g. “Emotet”, “Sofacy”, “cve-2017-11882”, “leaked builders”, etc.), the search will be executed not only against the IoC corpus (e.g. antivirus labels for files) but against the full VirusTotal knowledge base including actor/collection knowledge cards, online references and reporting, rules, graph investigations and community comments. The adversary intelligence content appears as a side block on search results listings, clicking on any of its items takes you to the pertinent knowledge card. Note that this functionality is only available to users with access to the Threat Landscape module.

- MITRE ATT&CK TTPs in threat {collection, actor} knowledge cards and open in MITRE ATT&CK Navigator. VirusTotal does not only aggregate detection engines but also dynamic analysis sandboxes. Mandiant CAPA and some of the sandboxes that we aggregate map out execution observations into MITRE ATT&CK tactics and techniques and Malware Behavior Catalog behaviors - see example report. When building threat {collection, actor} cards, VirusTotal aggregates all the mapped TTPs for all the IoCs linked to a given campaign/toolkit/actor and displays them in the TTP tab of the pertinent knowledge card. We’ve now included shortcuts to open these TTP mappings in MITRE ATT&CK Navigator.

- New and enhanced relations in VirusTotal’s underlying threat graph. VirusTotal provides superior context about IoCs. Some of that context is based on relationships with other IoCs and adversary entities, for example: contacted domains, download URLs, resolved IP addresses, compressed bundle parents, execution first stages, etc. We’ve enhanced VirusTotal’s core threat graph as follows:
- Added redirects to relationship. VirusTotal has been displaying target redirection URLs in the Details tab of URL reports for some time now, but this data point has never been added as a full-blown relationship displayed in the Relations tab and explorable via VT Graph. We have now rolled out the “redirects to” relationship.
- Enhanced embedded URLs relationship with memory pattern URLs. VirusTotal extracts URL patterns from the raw binary body of files and builds the embedded URLs relationship with them. This data point is very interesting but also very easy to evade via obfuscation, packing and some other common anti-analysis techniques. To overcome this, as we execute uploaded files in multiple sandboxes, we are now extracting URL patterns from memory and also feeding the embedded URLs relationship with them.

- VirusTotal Connectors. We’ve taken a significant step toward realizing the unified threat contextualization platform with VirusTotal Connectors. All your threat intel from third parties can now be seamlessly merged with VirusTotal's context. When faced with an unfamiliar file, hash, domain, IP address, or URL, having a singular view of threat intelligence not only expedites investigations but also helps eliminate detection blind spots. Learn more.

- File similarity summary view. The concept of similarity is pretty straightforward: are two files similar? There are many ways to figure it out. That's why different similarity algorithms exist. Now, why is this useful? Attackers need tools for their attacks, basically malware. Malware in the end is a piece of software, built from frameworks, code and libraries, and takes some time and expertise to create. The result is that two different malware files built from the same developer using the same pieces or builders will look alike. Tracking similar files often allows you to track actors or campaigns and study them proactively to build effective measures against such threats. VirusTotal has supported a number of file similarity searches for a while now (vhash, behash, imphash, ssdeep, TLSH, icon dhash, etc.). Earlier this year we rolled out some functionality to search across all different similarity approaches available for a file, the “Best candidates in a single search” trigger. Similarity search result listings now display a “Similarity details” toggle to better understand the common data points across matching files.

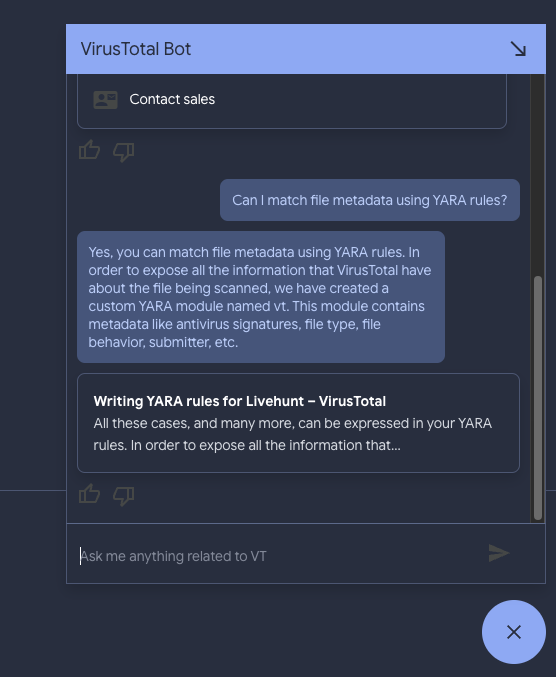
- Documentation chat assistant, a.k.a. VirusTotal bot. At VirusTotal we are committed to democratizing detection engineering and threat hunting. We acknowledge that VirusTotal Enterprise is a sophisticated tool and that not all organizations exhibit the same maturity when it comes to threat intelligence. We are now leveraging generative AI to accelerate our users’ maturity journey. Every single site within VirusTotal displays a small round floating message bubble in the bottom right hand corner. When clicking on it a chat dialog opens up. You can now ask questions (e.g. Can I match file metadata using YARA rules?) related to our documentation and it will summarize docs articles and point you in the right direction.
- Service accounts API documentation. Late last year we rolled out service accounts in order to interact programmatically with VirusTotal leveraging API keys that are not tied to individual users. We have now documented API endpoints related to VirusTotal API service accounts.
What has changed?
- McAfee-Gateway renamed to Skyhigh. Following McAfee Enterprise’s service renaming, the detection engine formerly known as McAfee-Gateway in VirusTotal has been renamed to “Skyhigh”.
What's new?
- File/URL response content strings searching. Other than a Threat Intelligence suite allowing its users to research world-wide emerging threat patterns, VT ENTERPRISE is also an automated malware analysis solution performing {reputational, static, dynamic, code, similarity} analysis of suspicious files. One of the static analysis components that runs on files is strings extraction, it runs on absolutely all uploaded files and VT ENTERPRISE users can both download files and see/download the strings for files uploaded by themselves or any other VirusTotal Community user. Moreover, strings extraction also acts on the content returned when checking URLs. We recently included functionality to download strings dumps for offline scrutiny, we are now extending strings-related capabilities with online search. Users can now search across file/URL response content strings within their browsers.

- VMRAY screenshots. VirusTotal not only analyzes files, domains, IP addresses and URLs with multiple antivirus vendors and blocklists, we also run a myriad of home-grown, open source and 3rd-party tools on these artifacts, including dynamic analysis sandboxes. Every executable (and other file formats) uploaded to VirusTotal gets detonated in both VirusTotal-developed and 3rd-party partner dynamic analysis environments to produce behavioral information such as domains contacted, payload download URLs, files created, registry keys set, etc. One of the 3rd-party sandbox vendor participating in this community effort is VMRay. VMRay has extended the data shared with VirusTotal to include screenshots produced during detonation, see example.

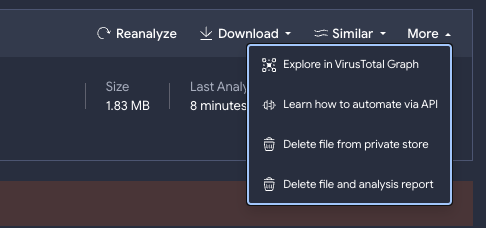
- Delete private files and analyses, via API or UI. VirusTotal Private Scanning allows its users to “see files through VirusTotal’s eyes” without making those files or their reports downloadable/visible to any 3rd-party beyond their own organizations, i.e. in a non-shareable fashion. All standard VirusTotal analysis components are included (reputation, static, dynamic - sandboxes, code, similarity analysis) except for multi-antivirus scanning. Private scans have a default 24h TTL both for uploaded files and their corresponding reports. Users also have the option to extend this TTL. We’ve now added additional API and UI actions allowing users to delete both files and their corresponding reports before the TTL is met.