What's new?
- SAML Authentication. Following our recent work on the SSO front,
we have now widely rolled out SAML to support federated login from a wider
range of identity providers. Among others, this allows organizations to
use popular services such as Okta to sign in to VirusTotal. If you are a
VT ENTERPRISE group administrator and you want to upgrade your team's account security please refer to the "Settings" tab of your VirusTotal group profile page:

- VT GRAPH revamp. VirusTotal is all about threat context. One of the pillars of context generation is IoC interlinking. We do not stop and providing threat reputation for individual IoCs, we try to build parent-child relationships between all the items in the dataset, e.g. a given file contacts a CnC domain, a URL downloads a given malicious file, etc. All these rich relationships can be explored visually in a single canvas with VT GRAPH, one of main components of VT ENTERPRISE. We have rolled out a new VT GRAPH version (learn more) incorporating:
- Filtering engine. Graphs are sometimes noisy, the new filtering wizard allows to easily and instantly (client-side) focus on nodes matching certain criteria, e.g. display only detected domains. AND/OR conditions are allowed.
- Expansion through VT Collections. Domains/IPs/URLs/files are now related to VT Collections, meaning that you can now pivot from a single IoC to a threat campaign/malware toolkit grouping to unearth additional IoCs that may not be directly tied to your starting point.
- Export a graph as a VT Collection. While graphs are fancy, it is difficult to action them in a corporate security stack. To ease this task we now allow you to export a graph into a VT Collection that can then be consumed via STIX and other standard formats in your SIEM/EDR/NDR/etc.
- Ubiquitous IoC contextualization. One of VirusTotal's major use cases is automated security telemetry enrichment (false positive discarding, true positive confirmation, alert/incident prioritization and alert/incident contextualization). VirusTotal has become the backbone of many SecOps flows, as a result, most security products have bring-your-own API key integrations to power enrichment use cases with our crowdsourced threat intelligence. This said, some of these integrations might be suboptimal in terms of overlaid context. Similarly, you might be using a niche product without off-the-shelf integration or you might not have administration permissions to activate certain enrichment plugins. We have revamped our VT4Browsers extension to solve this and provide superior threat context in a single pane of glass fashion across all your security products. The new functionality will automatically identify IoCs contained within websites of your choice and will incorporate VirusTotal's context to power faster and more accurate response.
- New "androguard_package" VT INTELLIGENCE search modifier. VT INTELLIGENCE
is often described as the Google for malware. It allows users to search
for IoCs and access superior context to understand threats. It also
allows users to perform reverse searches, i.e. to find files, URLs,
domains and IPs matching certain criteria. For example, users can search
for documents that launch powershell when opened, for files containing
certain binary/text patterns, for domains registered by a same
registrant, for URLs containing a given CnC panel path pattern, etc.
IoCs are also tagged with certain informative labels such as CVE numbers
for vulnerabilities that they exploit, file types, etc. We have
added a new search modifier for Android applications (APKs) that acts on the Android Package Name. Why is this useful?
- Tracking malware families. Attackers often leverage malware builders or simply recompile/repackage their malicious code to launch new attack instances. This leads to malware family variants exhibiting common properties, these commonalities can be used for detection and campaign monitoring purposes. See example.
- Brand impersonation monitoring. Attackers will often create fake apps impersonating renown brands and financial services. For instance, mobile banking trojans will pose as the legit banking app in order to deceive users into installing them and eventually intercept their banking credentials to perform fraudulent transactions. The new search modifier allows you to identify apps that are impersonating your brand. See example.
- Malicious IP address resolution call out in Domain reports. VirusTotal is not only about file reputation and file context, these days we have equally rich context on domains, IP addresses and URLs. Moreover, network IoCs tend to be more actionable than hashes as malware infrastructure tends to get reused across attacks and binary-distinct malware variants. Domain reports now highlight whether the domain last resolved to a detected IP address, without having to pivot to the IP address itself. This data point complements the domain reputation itself and can shed additional light whenever the domain itself is still undetected:
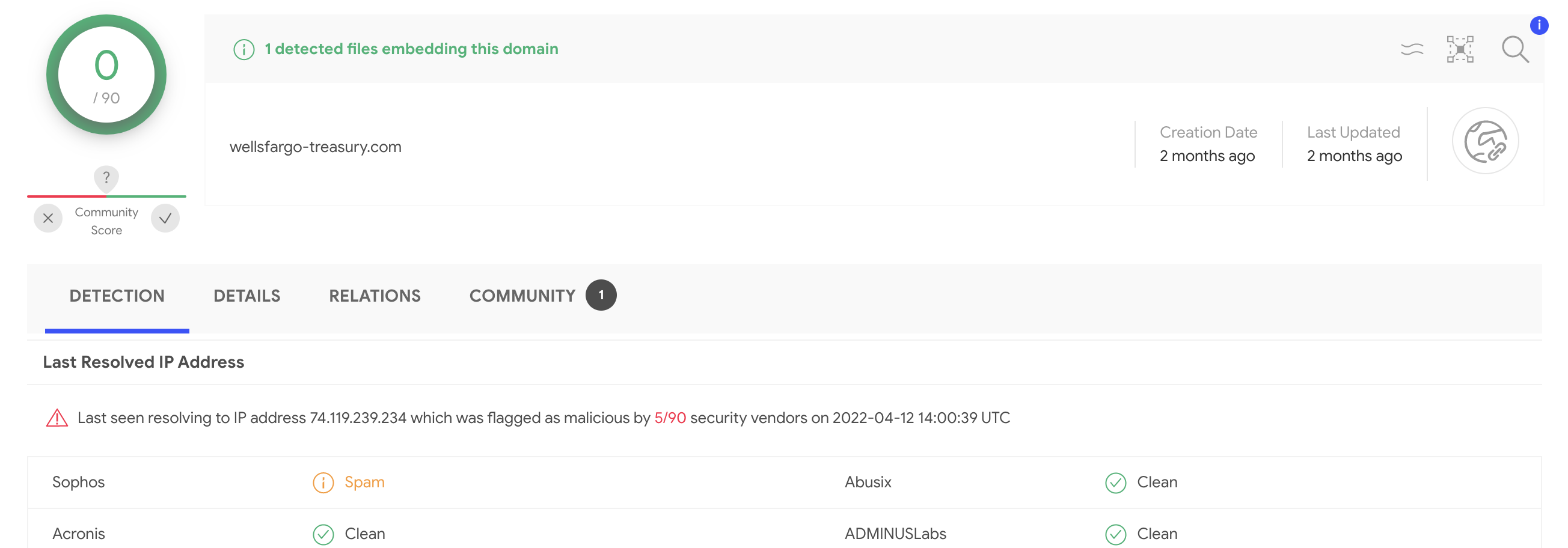
What's improved?
- Re-sending activation emails. Customers access VT ENTERPRISE with individual user accounts tied to a given corporate group. You can create a VirusTotal user account here. Upon signing up, an activation email is sent. Users that have not followed the activation link are not able to use the service. From time to time users miss this activation email or it ends up in some spam filter. If you now try to sign in with an inactive user account, you will be informed about the account state and the system will allow you to re-send the activation email.
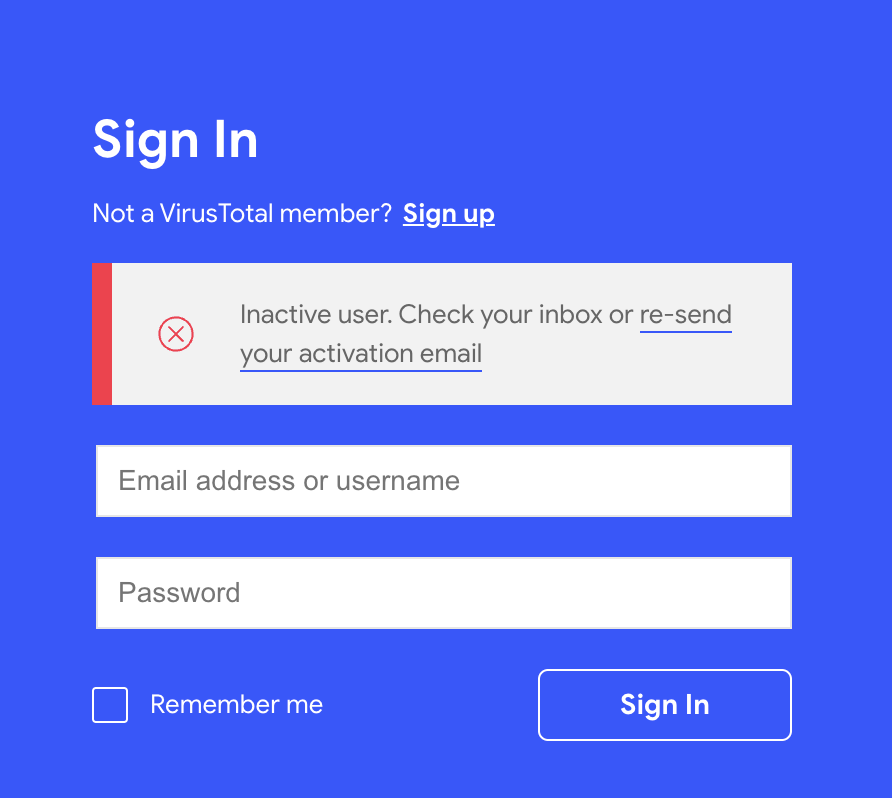
What's changed?
- Dynamic analysis Sysmon logs exported in XML format instead of binary. VT INTELLIGENCE is sometimes described as both a telescope for the threat landscape and a microscope for individual IoCs. Dynamic analysis of files submitted to VirusTotal (sandbox detonation) is one of the microscope-like capabilities. Moreover, VirusTotal aggregates multiple 3rd-party and home-grown sandboxes in order to improve visibility into threats, making cloaking more complex (different OS, different language packages, different software, distinct execution tracing techniques, etc.). VirusTotal's own home-grown sandboxes produce Sysmon execution logs that can be downloaded from VT INTELLIGENCE, alongside the network trace (PCAP), memory dump, detailed execution trace, etc. Sysmon traces were being exported in their raw binary format, we have changed this to XML, this results in two major improvements:
- Event data is streamed out of the sandbox machines in real time, this prevents missing data due to unfinished analyses or crashes.
- Better noise filtering as events can be automatically discarded in the sandbox itself.





