We are picking up our weekly release notes once again. This very first 2023 edition is a recap of noteworthy rollouts from the last months.
What’s new?
- New security vendor partnerships. VirusTotal is all about aggregating orthogonal threat detection and contextualization technologies in an effort to increase threat visibility and democratize knowledge about threats. We’ve been busy integrating new complementary vendors, including: ArcSight / Micro Focus (IP/domain/URLs), SOCRadar (IP/domain/URLs), DuskRise Cluster25 (IP/domain/URLs), PrecisionSec (IP/domain/URLs), Docguard (CDR/sandboxing), Deep Instinct (files), BKav PRO (files), Google (files), AI Spera / Criminal IP (IP/domain), Crowdsec (IP/domain/URL), AlphaSOC (IP/domain/URLs).
- Session expiration age and other enterprise readiness security controls. VirusTotal has been continually maturing on the enterprise readiness front, following our work on SSO/SAML or service accounts, we’ve been implementing advanced security controls such as:
- Custom session age - as an admin, check your group settings page.
- Custom inactivity timeouts - as an admin, check your group settings page.
- Latest account connections, to spot anomalous activity - only visible to each user, in their settings page.
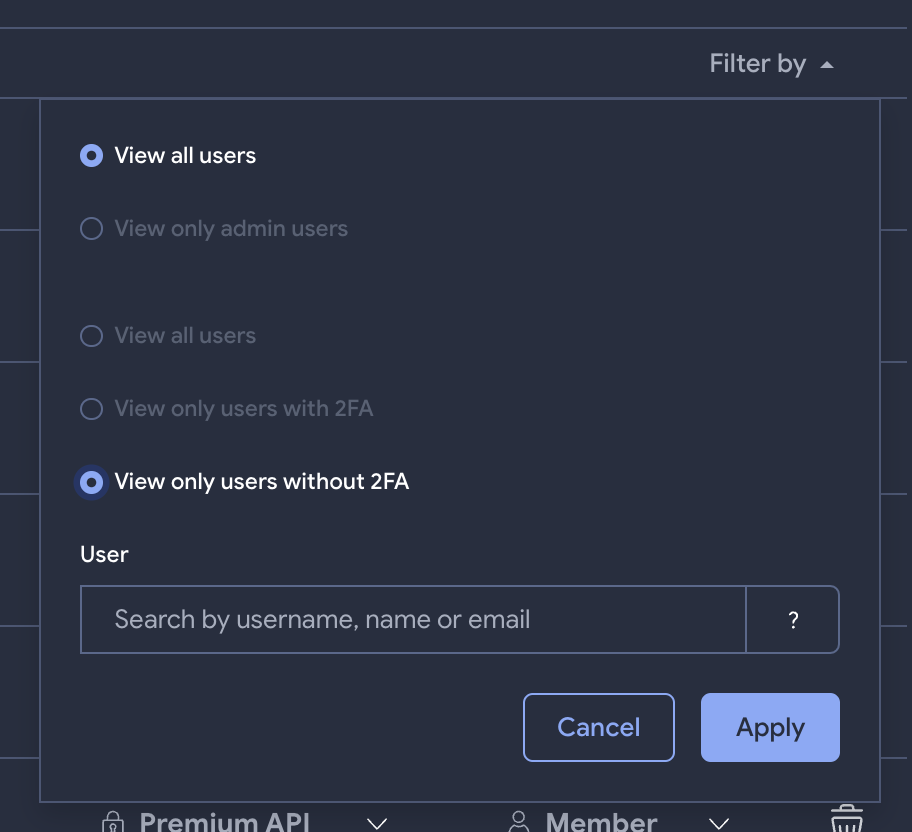
- Easier group and user management. Managing users within a VT group could be an arduous task for some group admins. To ease this task, we have incorporated the possibility to filter users by type (member or admin), username, name or email. Admins could also download a list of all VT users in the group in a CSV or JSON format.
- New VT Intelligence search modifiers and autocompletion. VT INTELLIGENCE is often described as the Google for malware. It allows users to search for IoCs and access superior context to understand threats. It also allows users to perform reverse searches, i.e. to find files, URLs, domains and IPs matching certain criteria. We have added support for the following new modifiers. Additionally, queries are now autocompleted, this should ease hunting and constant back and forth between VT ENTERPRISE and the search modifiers documentation.
- New properties in commonality calculations. When performing the aforementioned VT INTELLIGENCE reverse searches, or when looking at collections of IoCs, Retrohunts or other IoC listings, users can quickly understand what do the IoCs have in common in terms of technical static and dynamic features through the “commonalities” functionality. We are now aggregating and ranking new notions such as malware family names, C2s, etc:
- Extending VT ENTERPRISE with adversary intelligence. Since our last release notes we have rolled out adversary intelligence (attribution, threat actor profiling, campaign & toolkit knowledge cards) into our top VirusTotal packages, this new functionality is shipped under the Threat Landscape module and it allows users to climb the pyramid of pain, moving from IoC matching into more of operational/strategic intelligence through TTPs, behavioral patterns and adversary profiling. Learn more.

- IoC Stream as a vehicle to generate tailored relevant threat feeds. Building on the aforementioned new Threat Landscape module, we have rolled out the ability to subscribe or follow specific threat actors/campaigns/toolkits/incidents. When following a given threat entity, you get notified about any new IoC related to it. For instance, you would receive live notifications whenever a threat actor you are interested in starts to make use of a new command-and-control domain. These notifications now enter each user’s personal IoC stream, which is the pipe where all VT ENTERPRISE tailored IoC notifications are being centralized. Indeed, Livehunt YARA rule matches now also populate personal IoC streams. This creates an easy vehicle to generate custom feeds based on threats that matter to your organization, providing a centralized hub to receive all your notifications.
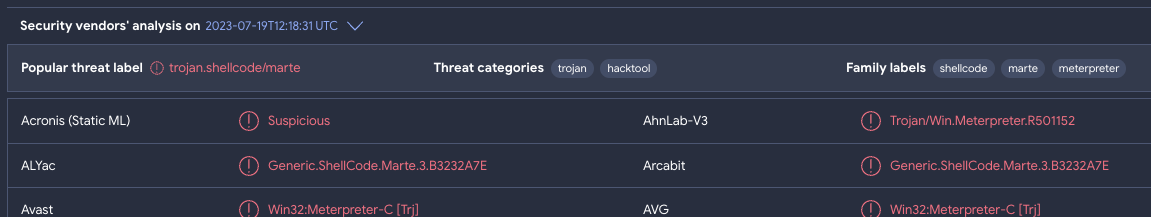
- Popular threat categories and labels. Security teams are often tasked with shedding light on the who/what/why/when/how of an incident. As part of this activity, identifying the malware family behind an attack is crucial for several reasons: understanding threat’s capabilities, tailoring incident response, attribution and tracking, risk assessment and impact analysis, etc. In order to accelerate malware family/toolkit identification we are now digesting multi-antivirus verdicts into overall popular categories and threat labels, ranked by prevalence, example. This data can also be retrieved programmatically via API.
- Improved malware configuration extraction. VirusTotal does not only analyze files, domains, IP addresses and URLs with multiple antivirus vendors and blocklists, we also run a myriad of home-grown, open source and 3rd-party tools on these artifacts. One of the dynamic analysis sandboxes in which we detonate uploaded files, Zenbox, has been automatically decoding/decrypting configuration files for known malware families for a while now (see “Malware configuration” section in the file analysis Details tab). We have extended this setup and added Mandiant’s Backscatter as yet one more system understanding common malware families and extracting configuration files, see example. Backscatter will identify malware families, C2s, decoys, dropzones, etc. The entire malware configuration output is pivotable (click on any of its fields) and a new search modifier (malware_config:) powers the search, example - malware_config:amadey. This effort will also soon be leveraged to tag network indicators with the corresponding family and infrastructure categorization.

for any technique in vt.behaviour.mitre_attack_techniques : (
technique.id == "t1012"
)
Last, but not least, we’ve included a shortcut on dynamic analysis reports to open these TTP mappings in
MITRE ATT&CK Navigator or to download them as a JSON and import them in similar tools. The shortcut is available in the “Download artifacts” dropdown and on the right of the MITRE ATT&CK section header.
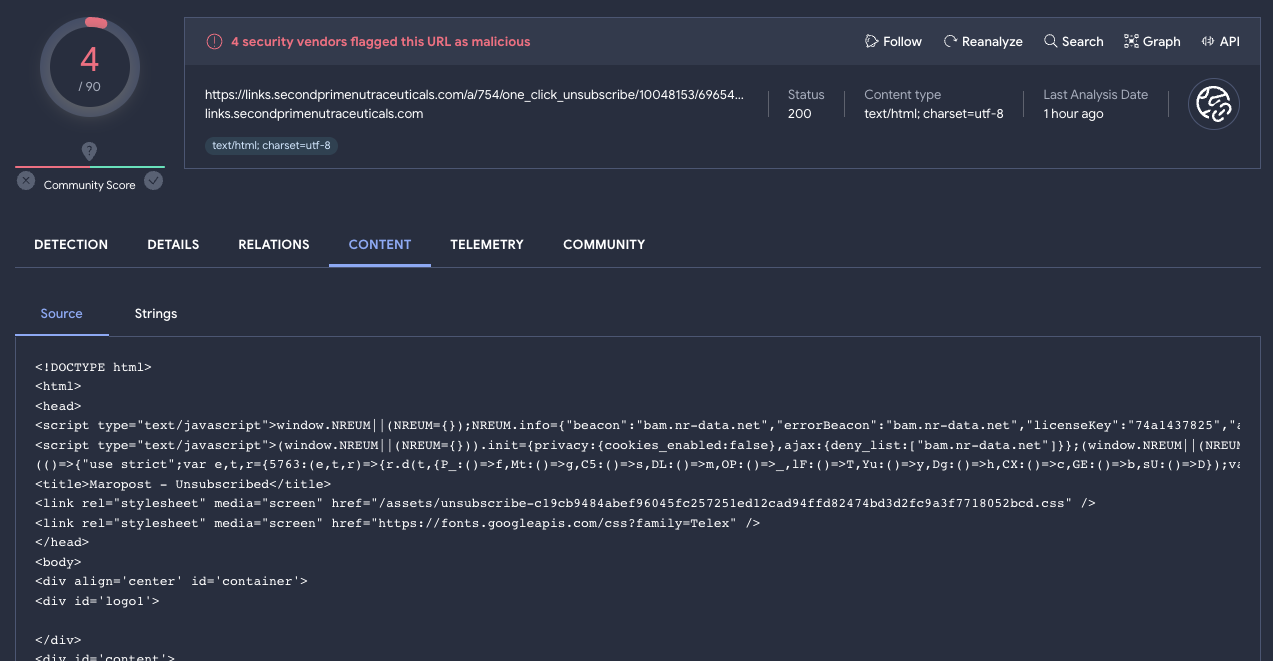
- HTTP response content preview for URL analyses. VirusTotal is not only about file scanning, it also contextualizes URLs, domains and IPs. Actually, these days VirusTotal’s most prevalent use case is around enriching network indicators. We are now mimicking some of the VT ENTERPRISE capabilities available for file reports and including HTTP response content previews in URL analyses, example. Most importantly, these responses are pivotable, meaning that users can click on any substring contained within the response and pivot to other files in VirusTotal’s threat corpus that contain the very same pattern, leveraging VTGREP. This is useful in tracking malware toolkit, campaigns and compromises at scale.
- New IP address tags: proxy, vpn and tor. Examples: entity:ip tag:proxy / entity:ip tag:vpn / entity:ip tag:tor. VirusTotal tags IoCs with relevant labels such as file types, packers, significant dynamic behaviors, etc. We are actually working towards an official tags taxonomy that can immediately contextualize IoCs in ways that may be easily consumed by both humans and machines. As part of such effort we have started to tag IP addresses with the proxy (residential proxies), vpn and tor (tor exit nodes) labels. These tags are dynamic and regularly updated. By enriching their security telemetry with VirusTotal lookups, these tags can help security teams in identifying attacker connections to their infrastructure. Indeed, certain threat groups often use residential proxies, VPNs or TOR nodes to connect to their victim’s infrastructure.
- New YARA rule editor. VT Hunting Livehunt allows VT Enterprise users to write YARA rules that are matched against the incoming live stream of files uploaded to VirusTotal. It has become a de-facto standard to monitor threat campaigns and malware toolkits, as well as to track threat actors going forward. Similarly, VT Hunting allows you to run these rules back in time against the historical corpus through a component called Retrohunt. Retrohunt allows you to map out threat campaigns, to find the first instance of an attack or to unearth unknown malware. To ease livehunting and retrohunting, we have rolled out a new YARA rule editor that incorporates rule templates, autocompletion, testing and validation.

- Crowdsourced YARA hub. Expanding on the above, YARA rules are an essential tool for detecting and classifying malware, and they are one of VirusTotal’s cornerstones. Other than using your own rules for Livehunts and Retrohunts, in VirusTotal we import a number of selected crowdsourced rules provided by contributors to help identify and classify samples (example report). However, finding, tracking and managing VirusTotal’s crowdsourced YARA rules can be challenging, especially as the number of rules and contributors grow. To address this, we’ve introduced VirusTotal’s Crowdsourced YARA Hub, allowing users to easily search and filter existing rules, track new ones and one-click export any of them to Livehunt and Retrohunt. This is also a vehicle to stay on top of new threats being investigated by the industry. Go to Crowdsourced YARA Hub.

- Official VirusTotal app for Splunk (VT4Splunk). VT4Splunk, VirusTotal’s official Splunk plugin, correlates your telemetry with VirusTotal context to automate triage, expedite investigations and unearth threats dwelling undetected in your environment. This extends Splunk’s own VirusTotal plugin for their SOAR.












.png)














.png)