What's new?

- Crowdsourced AI += NICS Lab. We’ve extended our Crowdsourced AI initiative with a generative AI model from a research group of the Computer Science Department at the University of Malaga. The new model processes PowerShell files, not only strengthening our collective understanding of the code and its behavior, but also providing verdicts on the potential threat level of each file - categorizing them as malicious, suspicious, or benign. See example.

- Keeping state around expansions and contractions of Behaviour sections. VirusTotal does not only run multiple antivirus/EDR solutions on files, it also brings together multiple sandbox dynamic analysis setups. These days we aggregate over 15 sandboxes covering 4 major operating systems (Windows, Linux, Android, OS X) and producing insights such as created/deleted files, registry keys set, contacted domains, synchronization mechanisms, etc. The output of these sandboxes is displayed in the Behavior tab of file reports. The information displayed in this tab is extremely exhaustive, we acknowledge that some users may only be interested in certain sections such as network communications. In order to improve relevance and discoverability, we are now storing state around section header contractions and expansions. This provides a personalized experience whereby upon loading new file reports users see the information that they deem important first.

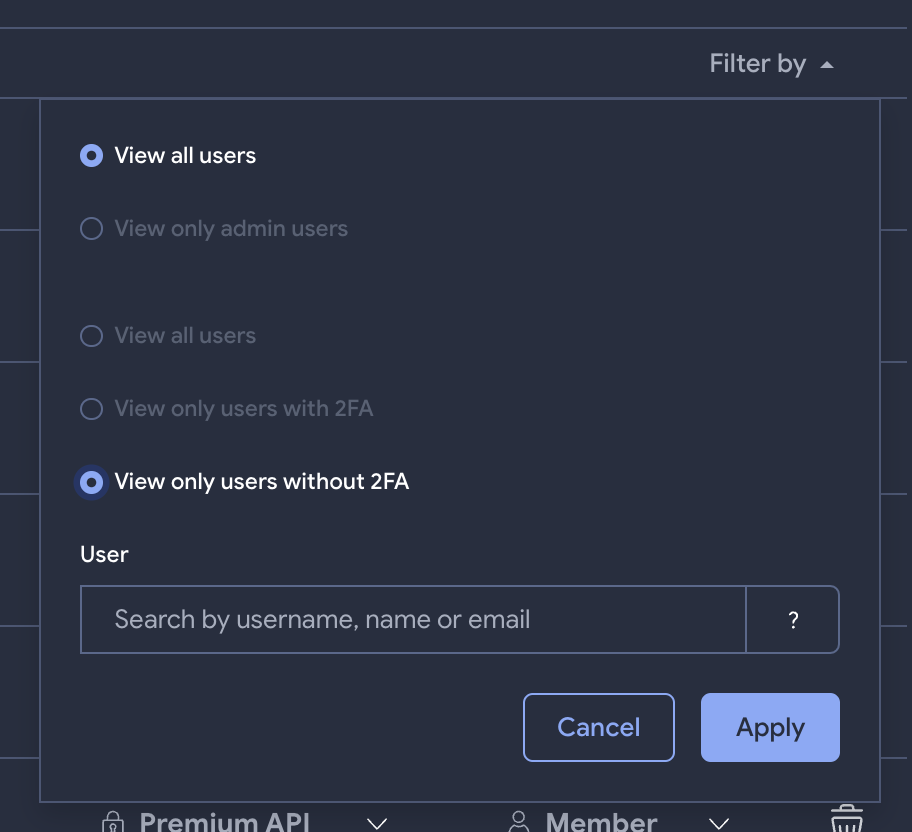
- Flags for users with active 2FA authentication and corresponding search filters. VirusTotal has been continually maturing on the enterprise readiness front, following our work on SSO/SAML or service accounts, we continue to improve security controls. Group administrators now see a “2FA” badge next to users with active two-factor authentication in group user listings. Similarly, administrators can also filter those listings to focus on users that have or do not have active 2FA.