What's new?
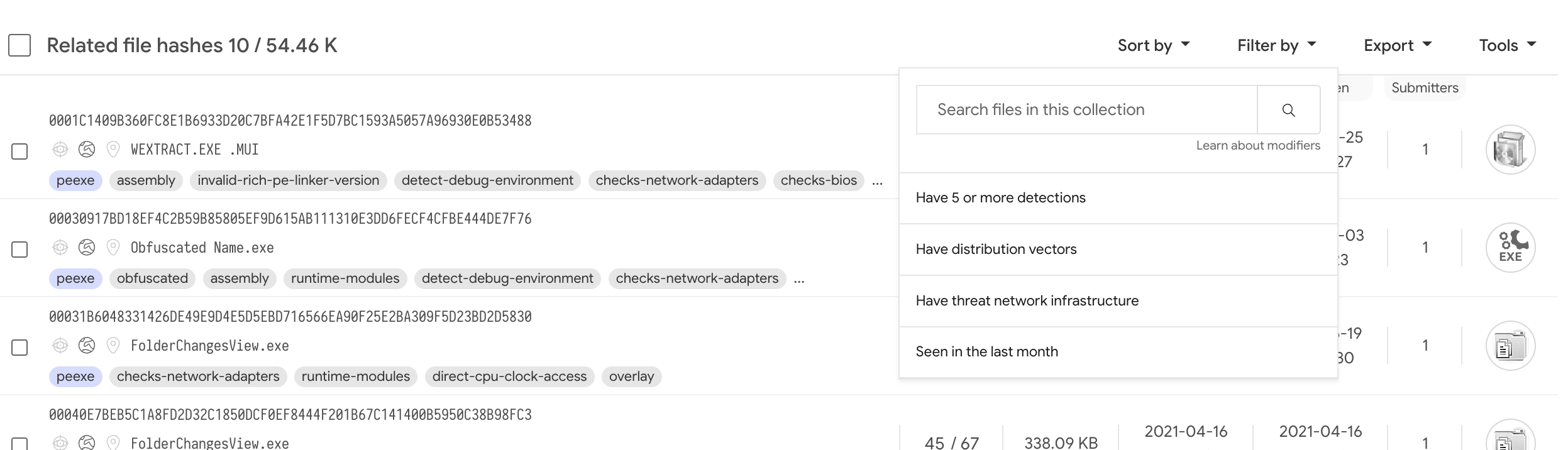
- Action menu for VirusTotal collections. VirusTotal Collections allows
users to share collections of IoCs (hashes, domains, IP addresses and
URLs) among themselves in a more actionable and contextualized manner.
You can read more about this in the Introducing VirusTotal Collections blog post, you can also easily create collections via command-line. We have added advanced sorting, filtering, exporting and analysis controls to collections. For example, users can now run minimal curation logic (detections > 5) prior to exporting a given collection when deploying the pertinent artifacts for IoC blocking/flagging in their SIEM, firewalls, protective DNS, etc.
- JARM pivoting in IP and Domain HTTPS certificates. VT INTELLIGENCE is often described as the Google for malware. It allows users to search for IoCs and access superior context to understand threats. It also allows users to perform reverse searches, i.e. to find files, URLs, domains and IPs matching certain criteria. We are adding support for JARM as a pivot property. JARM is an active Transport Layer Security (TLS) server fingerprinting tool. Among other things, it can be used to identify malware command and control infrastructure and other malicious servers on the Internet. VirusTotal sandbox detonation reports already contained JA3 digests, a passive TLS fingerprint, allowing users to find other files communicating with TLS using the same code stack, and thus often grouping together malware family variants. We are now extending such functionality to actively build a fingerprint (JARM) of Domains and IPs scanned by VirusTotal. This extends and complements our existing SSL certificate, whois lookup, DNS record, etc. pivots. The pivot can be found in Domain/IP address reports, under the "Last HTTPS Certificate" section of the "Details" tab. You can also action it by clicking on the similar icon in the top menu bar.

- New Linux partner sandbox, ELF Digest. VirusTotal not only analyzes files, domains, IP addresses and URLs with multiple antivirus vendors and blocklists, we also run a myriad of home-grown, open source and 3rd-party tools on these artifacts, including dynamic analysis sandboxes. Every executable (and other file formats) uploaded to VirusTotal gets detonated in both VirusTotal-developed and 3rd-party partner dynamic analysis environments to produce behavioral information such as domains contacted, payload download URLs, files created, registry keys set, etc. We have onboarded a new linux sandbox, ELF Digest, as part of the multisandbox.
What's improved?
- VirusTotal MISP modules. MISP, an open source threat intelligence platform, integrates with VirusTotal via three modules, two of which provide the essential enrichment functionality: virustotal and virustotal public. We have greatly revamped them in order to take advantage of the new context and threat graph exposed via our APIv3:
- Threat reputation (Detections) for domains and IPs, not only files/hashes and URLs.
- Clustering fingerprints such as imphash, TLSH, vhash, ssdeep, etc. allowing you to tie together similar IoCs.
- Extended static analysis including whois lookups, geoip location, autonomous system information, etc.
- Related artifacts via our threat graph: URLs from which a file is downloaded, files that communicate with a given domain when detonated in a sandbox, domains historically resolving to a given IP address (pDNS), etc.